

I’d say take some inspiration from Full Metal Alchemist as well, unless you haven’t watched FMA/FMA:Brotherhood yet. Then I’d say, watch that and then take inspiration from a particular episode.


I’d say take some inspiration from Full Metal Alchemist as well, unless you haven’t watched FMA/FMA:Brotherhood yet. Then I’d say, watch that and then take inspiration from a particular episode.


I play FFXIV and Warframe. I don’t have a PSN account and crossplay is fully functioning with both Playstation and Xbox users. Heck, Warframe is even available on Switch and crossplay works just fine with those users without any account linking.
I’ve used the oven method for two different gloves, but used shaving cream on the first one and a specific treatment foam on the second one. It’s been 10 years since I last played, but I remember putting it on a cookie sheet and we turned the oven off before placing the glove in.
Sucks this happened to ya. Hopefully somebody around you has a spare you can borrow until you can figure out a replacement and get it broken in.


I’m willing to bet they’re looking for the other version of mahjong


First, ask your boss for your employer’s policies on handling these situations.
Second, ask your boss for de-escalation training. If you’ve already gone through this training, a refresher will still be good.
Third, you mentioned a union. Ask them for recommendations and resources.
Fourth, if your concerns feel unaddressed, contact whomever would be your HR department. Know that HR is not there to help or protect employees, but there to keep the organization from being sued.
Fifth, do right by yourself. You’re obligated to your own safety. Healthcare is an emotionally charged environment with clients who are almost never there for good reasons. These high level emotions will cause intense feelings and scenarios. People can react irrationally during such situations.
Pretty much the only place selling XDA caps: https://kprepublic.com/collections/xda-profile


This would be correct. We have at least 7 amazon alexa/fireTV devices and a bunch of other IoT devices with Alexa capability and each of them get used regularly.
The IoT devices are on their own subnet which doesn’t have access to the other subnets. I live with my mom and Alexa devices just make her life way easier. I put in the work to make sure the alexa and IoT devices are as restricted as possible without losing functionality so she can live a bit easier.


Something is seriously wrong with your Windows 11 install. I have two Windows 11 devices on my network and a Surface Duo 2.
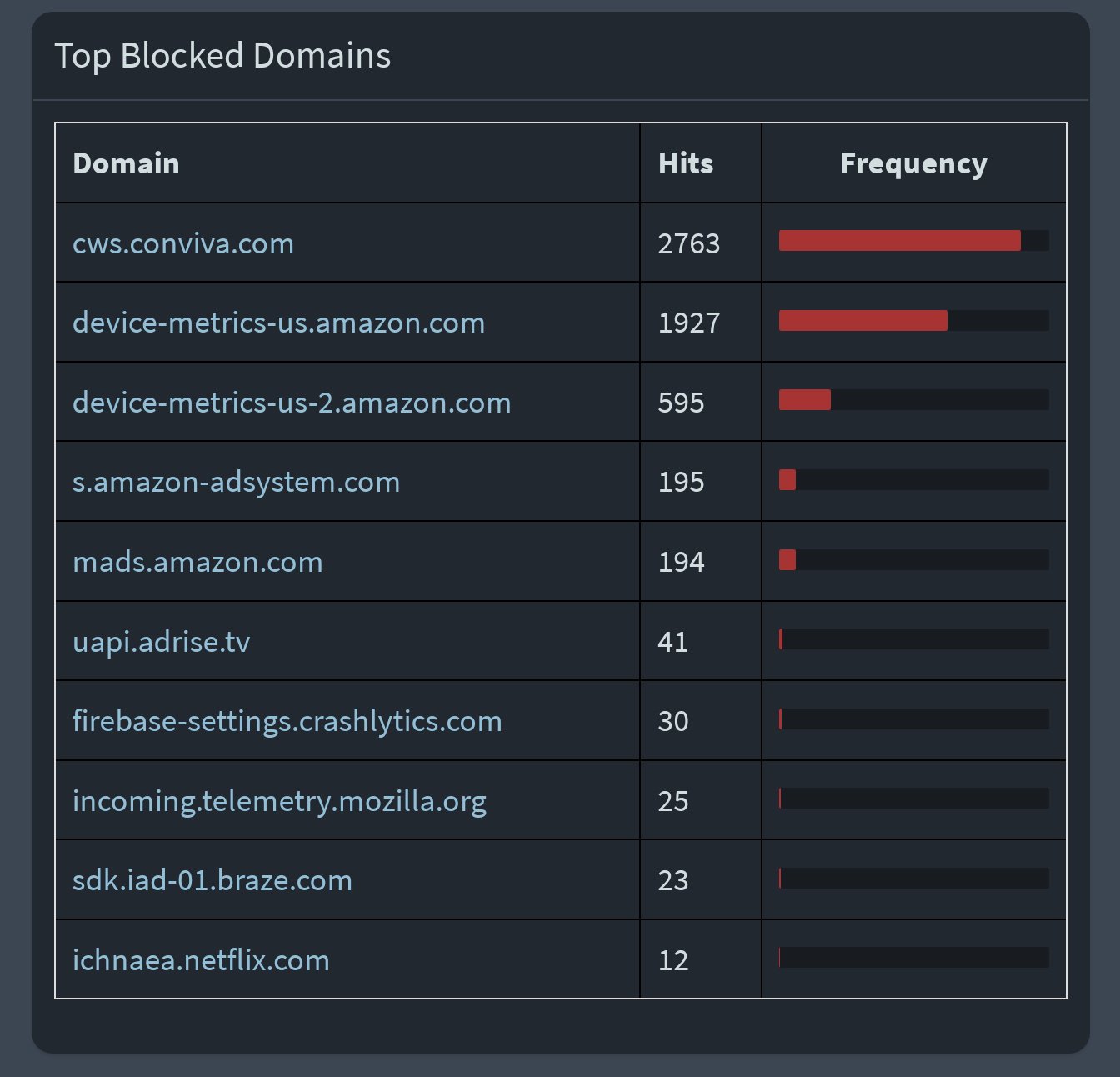


Netdata would be my recommendation, but that may be a little much for the situation. I have about 5 Debian VMs for different things and one of them is a netdata server I run which collects data from itself, the other VMs, a separate minipc I have for containers, and the host OS.
Otherwise, slap btop on there and watch the pretty terminal graph


Somebody at Godot knows how to make money


ADMIN, isn’t it time to move from lemmy.world?
They said, from their lemmy.world account.


It’s important to note that your password has to be stored someway, no matter what, no matter where. How it’s stored can be varied, from hashed (think encrypted) to cleartext. I’m assuming lemmy is using hashed passwords, so if you’re concerned about your password being available to an instance owner, admin, or potential attackers, then you’ll need to follow safe password guidelines. Changing the concept from passwords to passphrases is a great start.
Always keep in mind, if the data isn’t stored on your device, you do not technically own that data. You have to trust the owners to be good data custodians and treat the data you give them as if it were their own private data.
I’ll leave this now internet-ancient sacred image for future passphrase converts.

History of the World Part 1. An absolutely amazing Mel Brooks film


The old name is draw.io with the self-hosted version keeping that name. The current name is diagrams.net hosted on their servers.
In the end, it’s all the same


This might be out of scope for the list, but I thought of it after I saw your response.
Stride3d game engine: https://github.com/stride3d/stride


I don’t technically open any ports to the public. I have a site-to-site wireguard tunnel to a hosted server. The hosted server is running a hypervisor with two virtual switches. One switch is my external switch and only my Wireguard server is using it. The other is an internal switch where I place other VMs for separate things. A container host, a terminal server with xrdp, a monitoring server with netdata, stuff like that. All technically, but unnecessarily, accessed through nginx proxy manager.
Because it’s site2site with my home equipment on the Wireguard server, i can still connect to my home network where i host a number of separate services like HomeAssistant from outside the home network.
I don’t use tailscale, but Wireguard vanilla is super easy to work with. I also have fail2ban pretty much everywhere I can install it because it takes up practically zero resources.


For monitoring, i didn’t see Zabbix or Netdata:
https://git.zabbix.com/projects/zbx/repos/zabbix/browse
https://github.com/netdata/netdata
I also didn’t see OBS for broadcasting either:


For real, man. Homegrown tomatoes are fkn delicious.
I know you already found a solution, but fwiw, it seems you have a typo in calling the extension. You have “stats” plural instead of “stat” singular.